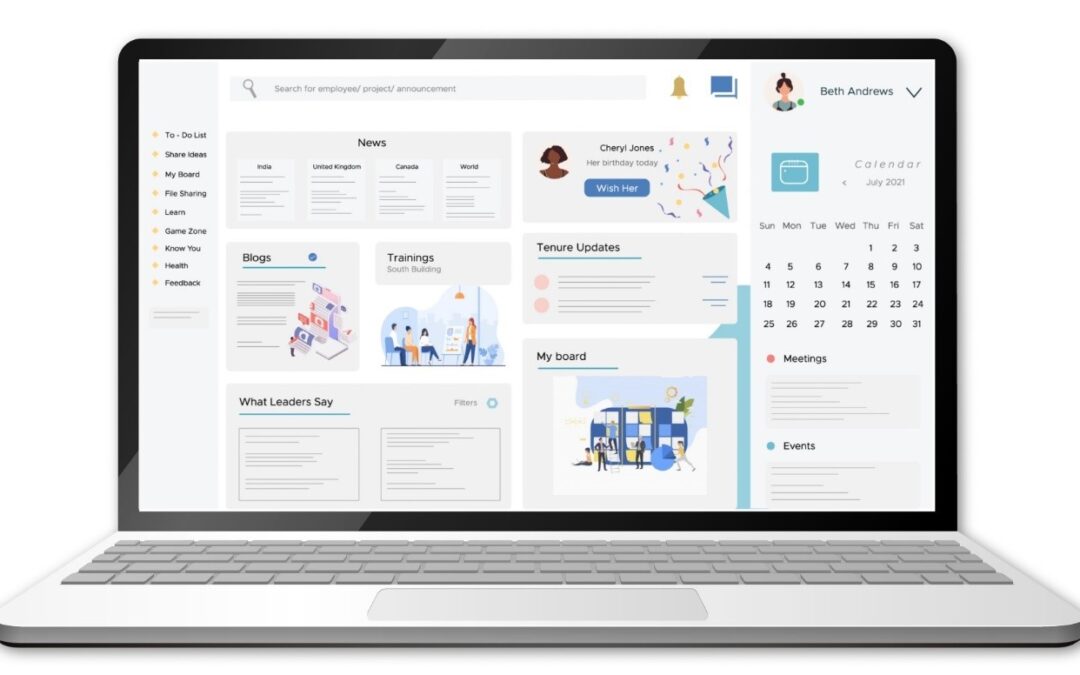
by María Martin Pognante | Sep 23, 2024 | Business Transformation, Cyber Security, Data Science & Analytics, Innovation
Wondering what the whole buzz of INTRANET is about? Here we answer the top 9 FAQs about the intranet. 5 min Read TOP 9 FAQs About the Intranet What does Intranet mean? Why is an Intranet important? Where is an Intranet used? Can an Intranet be hacked? Is an Intranet...
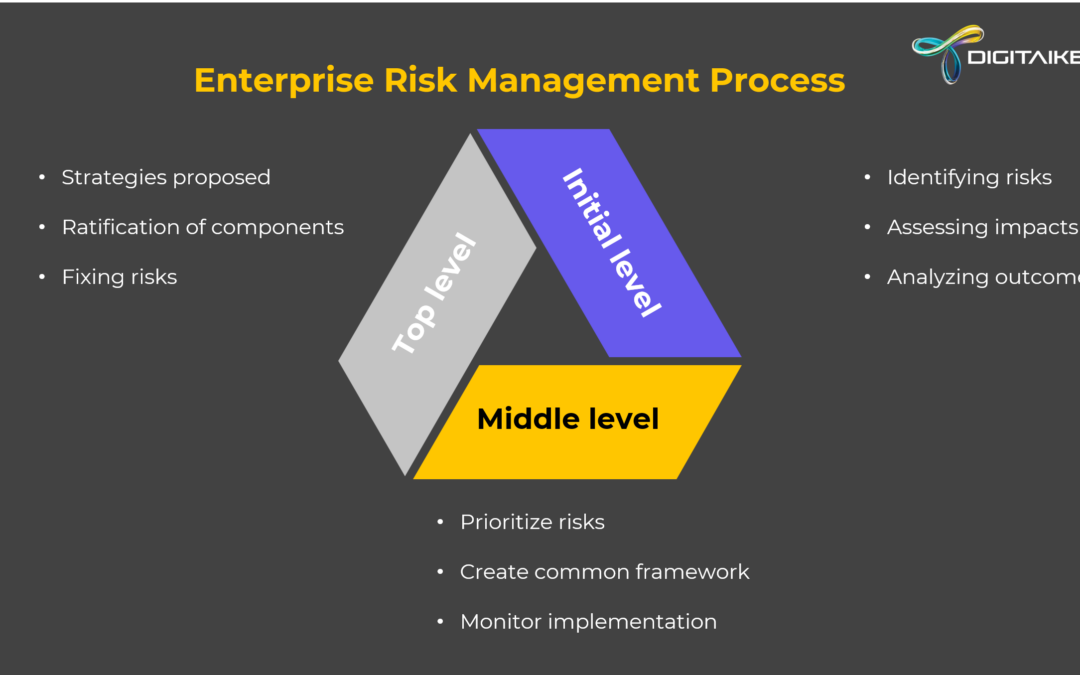
by María Martin Pognante | Sep 23, 2024 | Business Transformation, Cloud Optimisation, Cyber Security, Data Science & Analytics, Data Strategy, FinOps, Identity and Access Management (IAM), Innovation
Risk is becoming a major worry for everyone. CEOs who have recently been surveyed continue to identify numerous hazards to their organisations. Some of the main issues mentioned are technological development, geopolitical unpredictability, cybercrime, and the...
by María Martin Pognante | Sep 23, 2024 | Automation, Business Transformation, Cloud Optimisation, Cyber Security, Data Strategy, Identity and Access Management (IAM), Innovation, Low Code
In this ever-changing world, businesses need to keep up with these changes or be left behind. 64% of business executives believe their companies need to build new strategies around digitization to remain viable and sustain productivity through 2023, while only 11% say...

by María Martin Pognante | Sep 23, 2024 | Business Transformation, Computer Vision & AI, Cyber Security, Data Science & Analytics, Ideation & Prototyping, Identity and Access Management (IAM), Innovation, IoT
Digitization is becoming more and more important in today’s world. In this article, we explore why CIAM is crucial for businesses undercoming this transformation. Your business should evolve along with technology. At this stage, deciding how to transform an...

by María Martin Pognante | Sep 23, 2024 | Business Transformation, Cyber Security, Data Strategy, Identity and Access Management (IAM)
In today’s interconnected digital landscape, where data breaches and cyber threats are on the rise, organizations face significant challenges in safeguarding sensitive information and maintaining regulatory compliance. Identity governance has emerged as a...







